This section needs expansion with: Remote desktop software Comparison of remote desktop software. Additionally the server program could be customized before being delivered by a so-called server editor an idea borrowed from Back Orifice Sub7 was originally written by a programmer with the handle "mobman". Views Read Edit View history. From Wikipedia, the free encyclopedia. The Trojan itself has been Trojaned". 
| Uploader: | Turan |
| Date Added: | 15 August 2018 |
| File Size: | 42.34 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 89762 |
| Price: | Free* [*Free Regsitration Required] |
As one security book phrased it: Nearly all antivirus programs can detect Sub7 and prevent it from being installed unless steps are taken to hide it.
Unsourced material may be challenged and removed. Remote desktop software Comparison of remote desktop software. The strange tale of the zub7legends of service attacks on grc. This page was last edited on 1 Juneat The Trojan itself has been Trojaned".
Sub7legends zip download
Because its typical use is to allow undetected and unauthorized access, Sub7 is usually described as a trojan horse by security experts. You can help by adding to it. Additionally the server program could be customized before being delivered by a so-called server editor an idea borrowed from Back Orifice sub7legneds No development had occurred in several years until a new version was scheduled for release sub7legneds Feb.
Articles needing additional references from April All articles needing additional references Articles to be expanded from January All articles to be expanded Articles using small message boxes All articles with unsourced statements Articles with unsourced statements from March It was very buggy and was not written in Delphi which the original author used.
Like other remote admin programs, Sub7 is distributed with a server and a client. Ina hacker began distributing a Spanish-language email purporting to be from security firm Symantec that was used to trick recipients sub7legemds downloading Sub7.
SubSeven has been used to gain unauthorized access to computers. Sub7 has not been maintained since Views Read Edit View history.
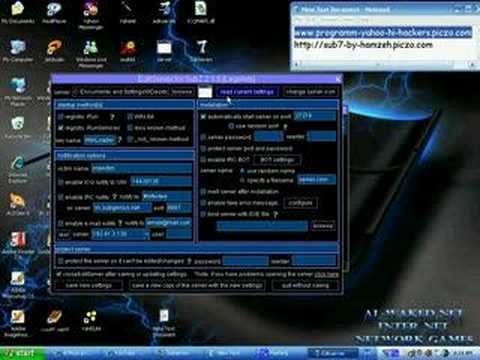
On the client-side the software had an "address book" that allowed the controller to know when the target computers are online. Sub7 worked on the Windows 9x and on the Windows NT family of operating systems, up to and including Windows 8. According to a security analysis, [8] Sub7's server-side target computer features include:.
This section needs expansion with: From Wikipedia, the free encyclopedia. Please help improve this article by adding citations to reliable sources.
Sub7 - Wikipedia
Sub7 has more features than Netbus webcam capture, multiple port redirect, user-friendly registry editor, chat and more sub7ldgends, but it always tries to install itself into windows directory and it does not have activity logging. The website that claimed to do this is no longer active. The Killer Web Applications. For the band, see Subseven.
Connections to Sub7 servers can be password protected with a chosen password. This article needs additional citations for verification. While it can be used for making mischief such as making sound files play out of nowhere, change screen colors, etc.
Sub7legends download
Sub7 is so invasive, he said, that anyone with it on their computer "might as well have the hacker standing right next to them" while using their computer. By using this site, you agree to the Terms of Use and Privacy Policy.
Retrieved from " https: Windows remote administration software Remote administration software Trojan horses Pascal software.

No comments:
Post a Comment